一、简介
众所周知,K8S拥有强大的RBAC权限管理策略,ClusterRole、Role可以精确区分角色权限 在日常使用中,我们常用kubectl工具进行集群管理,kubectl通过读取kubeconfig文件获取集群信息、集群证书信息,用户信息等。一般情况下部署好的k8s提供kubeconfig拥有最高的权限。 本文将介绍如何修改kubeconfig文件,使kubectl拥有指定的权限
二、创建ServiceAccount
这里我们需要先创建一个用户,用于k8s认证
apiVersion: v1
kind: ServiceAccount
metadata:
name: user
namespace: default
三、创建Role
创建角色,这里使用Role创建、当然您可以使用默认的ClusterRole或者创建的ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: user-role
namespace: default
rules:
- apiGroups: [""]
resources: ["pods", "pods/exec"]
verbs: ["get", "list", "watch", "create", "delete", "update", "patch"]
四、创建RoleBinding
角色和用户绑定,这里使用RoleBinding,您也可以使用ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: user-access-default-namespace
namespace: default
subjects:
- kind: ServiceAccount
name: user
namespace: default
roleRef:
kind: Role
name: user-role
apiGroup: rbac.authorization.k8s.io
五、创建Secret
根据K8S版本特性,新版K8S创建ServiceAccount后会生成secret,如果自动生成则或忽略此步骤。 如没有生成,可参照如下yaml
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: user-token
annotations:
kubernetes.io/service-account.name: "user"
namespace: default
六、修改kubeconfig
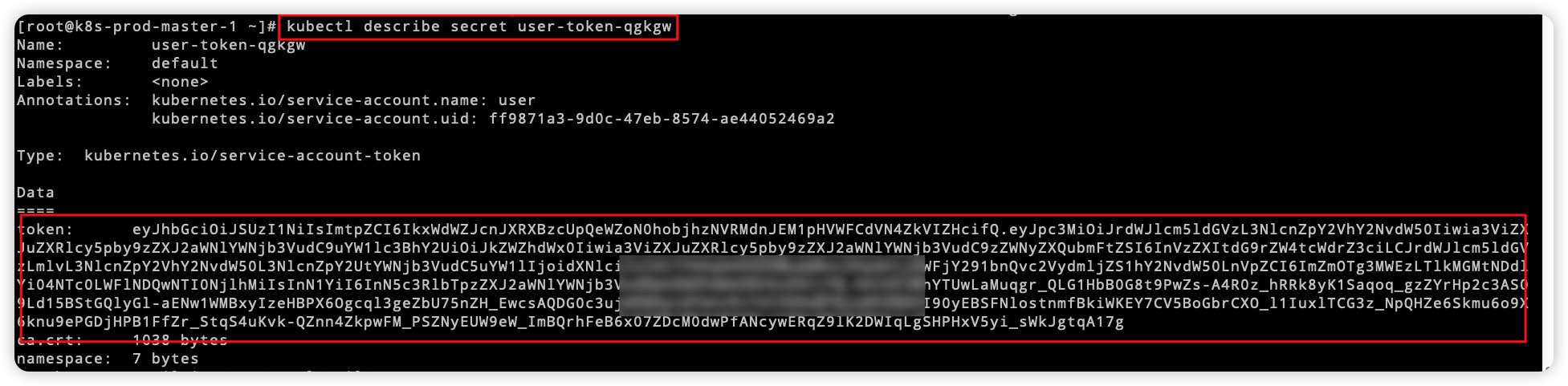
6.1 获取用户token
第五节中创建secret后会生成token,使用kubectl describe secret xxx查看token,如图:
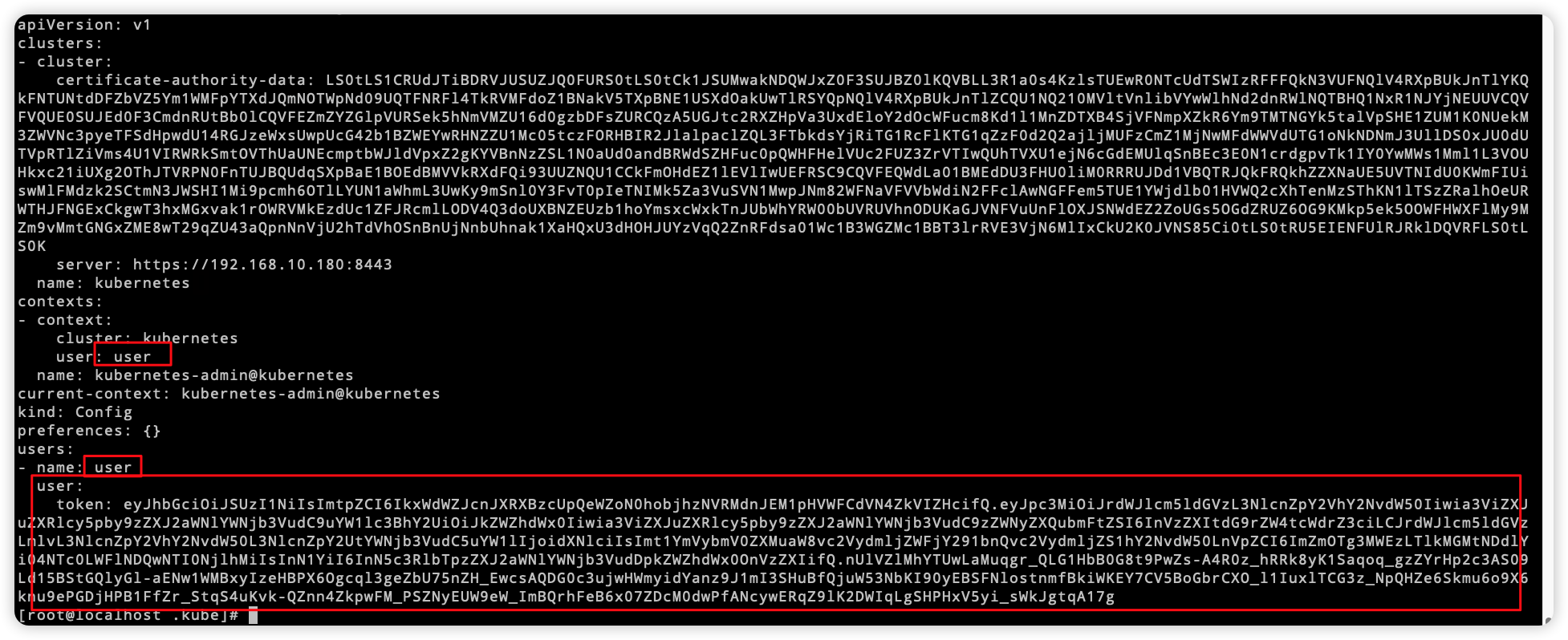
6.2 修改kubeconfig
将用户及token复制到kubeconfig内
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMwakNDQWJxZ0F3SUJBZ0lKQVBLL3R1a0s4KzlsTUEwR0NTcUdTSWIzRFFFQkN3VUFNQlV4RXpBUkJnTlYKQkFNTUNtdDFZbVZ5Ym1WMFpYTXdJQmNOTWpNd09UQTFNRFl4TkRVMFdoZ1BNakV5TXpBNE1USXdOakUwTlRSYQpNQlV4RXpBUkJnTlZCQU1NQ210MVltVnlibVYwWlhNd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3CmdnRUtBb0lCQVFEZmZYZGlpVURSek5hNmVMZU16d0gzbDFsZURCQzA5UGJtc2RXZHpVa3UxdEloY2dOcWFucm8Kd1l1MnZDTXB4SjVFNmpXZkR6Ym9TMTNGYk5talVpSHE1ZUM1K0NUekM3ZWVNc3pyeTFSdHpwdU14RGJzeWxsUwpUcG42b1BZWEYwRHNZZU1Mc05tczFORHBIR2JlalpaclZQL3FTbkdsYjRiTG1RcFlKTG1qZzF0d2Q2ajljMUFzCmZ1MjNwMFdWWVdUTG1oNkNDNmJ3UllDS0xJU0dUTVpRTlZiVms4U1VIRWRkSmtOVThUaUNEcmptbWJldVpxZ2gKYVBnNzZSL1N0aUd0andBRWdSZHFuc0pQWHFHelVUc2FUZ3ZrVTIwQUhTVXU1ejN6cGdEMUlqSnBEc3E0N1crdgpvTk1IY0YwMWs1Mml1L3VOUHkxc21iUXg2OThJTVRPN0FnTUJBQUdqSXpBaE1BOEdBMVVkRXdFQi93UUZNQU1CCkFmOHdEZ1lEVlIwUEFRSC9CQVFEQWdLa01BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRQkhZZXNaUE5UVTNIdU0KWmFIUiswMlFMdzk2SCtmN3JWSHI1Mi9pcmh6OTlLYUN1aWhmL3UwKy9mSnl0Y3FvT0pIeTNIMk5Za3VuSVN1MwpJNm82WFNaVFVVbWdiN2FFclAwNGFFem5TUE1YWjdlb01HVWQ2cXhTenMzSThKN1lTSzZRalhOeURWTHJFNGExCkgwT3hxMGxvak1rOWRVMkEzdUc1ZFJRcmlLODV4Q3doUXBNZEUzb1hoYmsxcWxkTnJUbWhYRW00bUVRUVhnODUKaGJVNFVuUnFlOXJSNWdEZ2ZoUGs5OGdZRUZ6OG9KMkp5ek5OOWFHWXFlMy9MZm9vMmtGNGxZME8wT29qZU43aQpnNnVjU2hTdVhOSnBnUjNnbUhnak1XaHQxU3dHOHJUYzVqQ2ZnRFdsa01Wc1B3WGZMc1BBT3lrRVE3VjN6MlIxCkU2K0JVNS85Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
server: https://192.168.10.180:8443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: user
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: user
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkxWdWZJcnJXRXBzcUpQeWZoN0hobjhzNVRMdnJEM1pHVWFCdVN4ZkVIZHcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InVzZXItdG9rZW4tcWdrZ3ciLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoidXNlciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImZmOTg3MWEzLTlkMGMtNDdlYi04NTc0LWFlNDQwNTI0NjlhMiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OnVzZXIifQ.nUlVZlMhYTUwLaMuqgr_QLG1HbB0G8t9PwZs-A4R0z_hRRk8yK1Saqoq_gzZYrHp2c3AS09Ld15BStGQlyGl-aENw1WMBxyIzeHBPX6Ogcql3geZbU75nZH_EwcsAQDG0c3ujwHWmyidYanz9J1mI3SHuBfQjuW53NbKI90yEBSFNlostnmfBkiWKEY7CV5BoGbrCXO_l1IuxlTCG3z_NpQHZe6Skmu6o9X6knu9ePGDjHPB1FfZr_StqS4uKvk-QZnn4ZkpwFM_PSZNyEUW9eW_ImBQrhFeB6x07ZDcM0dwPfANcywERqZ9lK2DWIqLgSHPHxV5yi_sWkJgtqA17g